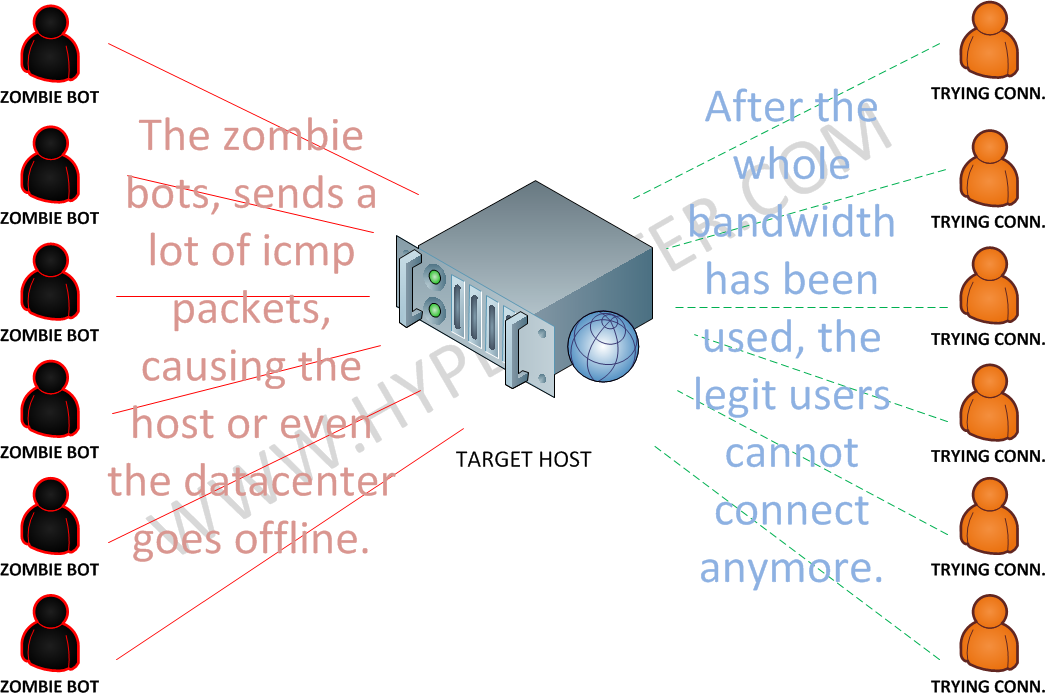
How does this attack type works ?
- This attack is focused to overwhelm the target host resources.
What does it means in practical terms ?
- Within this attack type, generally your server will just become unavailable for any type of external request that try to legitimately connect to any of your services.
- It may use or not, all the available bandwidth on your host or datacenter.
- In this case, while this attack is being performed, you may notice a high cpu, network and memory usage.
- The zombie bots in the example, can either be infected regular user computers or compromised servers in any organization.
- You can learn more about this icmp attack : clicking here
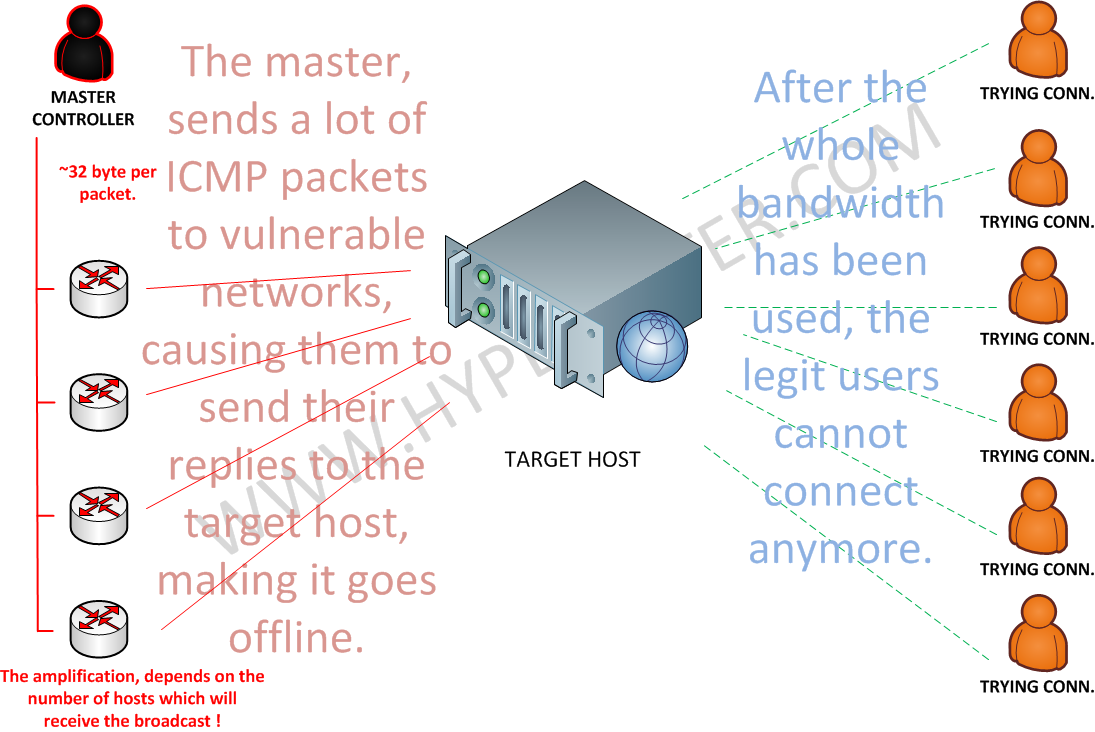
How does this attack type works ?
- This attack is focused to use the whole target host or datacenter available bandwidth.
What does it means in practical terms ?
- Within this attack type, generally your server will just become unavailable for any type of external request that try to legitimately connect to any of your services.
- It will use all the available bandwidth on your host or datacenter until everything becomes offline.
- The main characteristic of this attack, is that the master will control a list of several compromised networks, which may amplify the ICMP echo requests.
- While the amplification factor, is smaller compared to the UDP DNS Amplification method, it is still very effective accomplishing the proposed task.
- The zombie bots in the example, can either be infected regular user computers or compromised servers in any organization.
- You can learn more about this icmp attack : clicking here
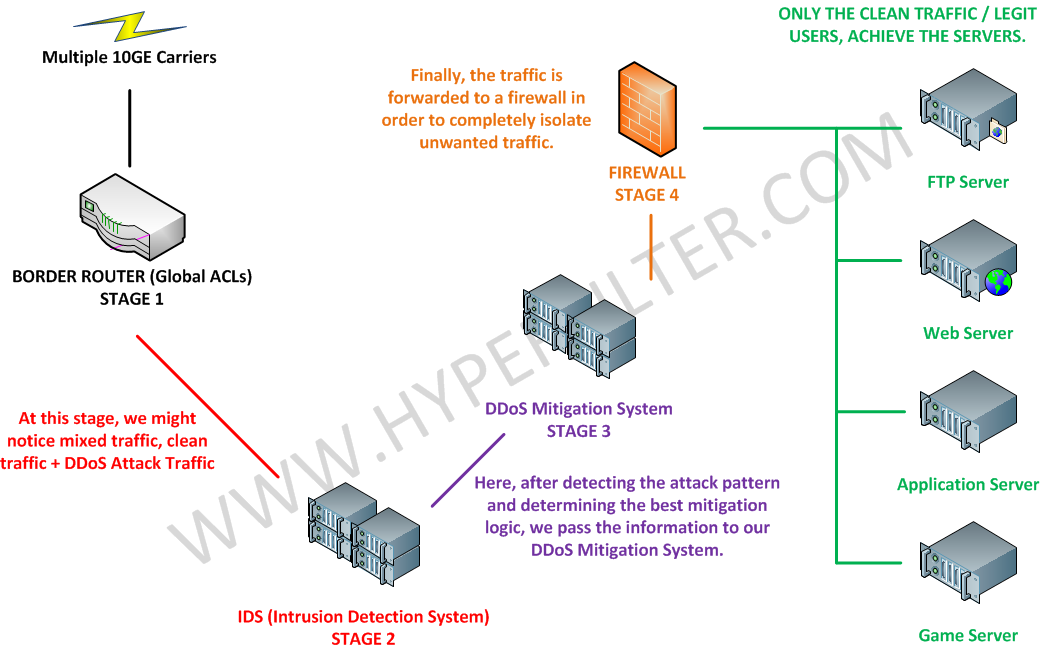
It is easy, we have specializing engineers in the DDoS Mitigation area !
- We are used to solve these types of attack daily with our customers, with our automated systems !
What does it means in practical terms ?
- Generally these DDoS Attacks are solved with a quad stage mitigation system as shown in the picture.
- There aren’t any noticeable latency constraints with the usage of our DDoS Mitigation technology.
- We have a large know-how in this area, which means you can be safe, that whenever a new issue raises our team will be able to solve it !
HyperFilter DDoS Protection SolutionsHyperFilter DDoS Protection Solutions
2013-08-25 17:00:56-05:00
2016-09-18 10:06:59-05:00